Chapter 7. Basic Firewall Configuration
During the Red Hat Linux installation, you are given the option to choose high, medium or no security level as well as allow specific devices, incoming services, and ports. These levels are based on the GNOME Lokkit firewall configuration application.
After installation, you can change the security level of your system by using GNOME Lokkit.
GNOME Lokkit allows you to configure firewall settings for an average user by constructing basic ipchains networking rules. Instead of having to write the rules, this program asks you a series of questions about how you use your system and then write it for you in the file /etc/sysconfig/ipchains.
You should not try to use GNOME Lokkit to generate complex firewall rules. It is intended for average users who want to protect themselves while using a modem, cable, or DSL Internet connection. To configure specific firewall rules, refer to the Firewalling with iptables chapter in the Official Red Hat Linux Reference Guide.
To disable specific services and deny specific hosts and users, refer to Chapter 8.
To start GNOME Lokkit, type the command gnome-lokkit at a shell prompt as root.
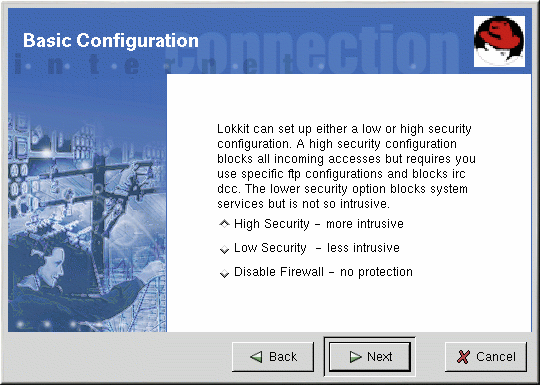
Basic
After starting the program, choose the appropriate security level for your system:
High Security — This option disables almost all network connects except DNS replies and DHCP so that network interfaces can be activated. IRC, ICQ, and other instant messaging services as well as RealAudioTM will not work without a proxy.
Low Security — This option will not allow remote connections to the system, including NFS connections and remote X Window System sessions. Services that run below port 1023 will not accept connections, including FTP, SSH, Telnet, and HTTP.
Disable Firewall — This option does not create any security rules. It is recommended that this option only be chosen if the system is on a trusted network (not on the Internet), if the system is behind a larger firewall, or if you write your own custom firewall rules. If you choose this option and click Next, proceed to the section called Activating the Firewall. The security of your system will not be changed.